|
: Spam Warrior :
: Lately (as in the past few months [Ed.: Summer
2001]), I've been receiving literally gobs
: of spam. It's not your ordinary spam (although I get a little of that
: too). These are spam/viruses, most notably the Hybris worm, on which
: there's some excellent
information online.
: However, I'm attempting to fight back using what tools
are available.
: The interactive portion of this piece is that I'm going to walk you
: through what I'm doing (i.e. you're going to do it too).
: Here's a list of the date, IP, carrier and country from
which I've received
: a spam/virus over the course of a few days in July.
| 7.12 |
211.3.232.66 |
Japan Telecom |
Japan |
| 7.12 |
200.203.141.82 |
Brazil Telecom |
Brazil |
| 7.12 |
148.221.152.131 |
Telefonos de Mexico |
Mexico |
| 7.12 |
217.227.30.7 |
Deutsche Telekom AG |
Germany |
| 7.12 |
202.108.44.206 |
Chinanet-BJ of China Telecom |
China |
| 7.13 |
212.23.253.116 |
Colt Telecom AG |
Switzerland |
| 7.14 |
213.132.137.246 |
TVD Internet |
Belgium |
| 7.15 |
202.96.154.20 |
Chinanet Guangdong Province of China Tel. |
China |
| 7.15 |
213.6.250.93 |
MobilCom Cityline GmbH |
Germany |
| 7.15 |
63.144.65.127 |
Qwest Communications |
USA |
| 7.15 |
202.158.92.211 |
PT. Cyberindo Aditama |
Indonesia |
| 7.15 |
164.77.129.11 |
??? |
??? |
: [Update] I'm also maintaining a more
complete log of all IP spamming me to date.
: Alright, let's get to work!
: Getting started :
: You'll need to find the IP address of an email you want
to trace. If you're
: on a Windows machine and/or using Outlook Express, this step is very
: dangerous. As far as I know, there's no way to get the originator's
IP
: without openning an email. Since I'm on a Mac, I'm pretty safe from
: most virii.
:The first thing you want to do is to display the full
header that came with
: the email.
: Handily enough, I just now received another Hybris worm
for me to use
: as an example. The Spam Gods must be smiling on me today!
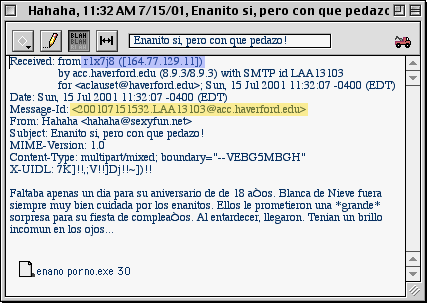
Hybris.gif
: I'm using Eudora, so I've displayed the full message
header by toggling
: the "Blah Blah Blah" button. In Outlook, select the message
and choose
: Edit > Properties. Not sure how to do it in Netscape.
: I've highlighted the important information. In blue
we have the originator's
: server name (the domain name entry) and the IP address. In yellow
we
: have the message ID that the server acc.haverford.edu used to log
the
: message transmission.
: (You might have noticed that I've now received 30 attachments named
: "enano porno.exe" !)
: Stalking the Spammer :
: With the originator's IP address in hand, we hop over
to
: http://samspade.org to do the dirty
work. You can do this from your own
: computer, but samspade provides many handy tools with a web-interface.
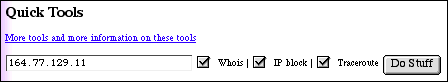
samSpade_start.gif
: I first conduct a Whois query, an IP block query and
a Tracerout. The Whois
: query returns ownership information that sometimes contains information
: about who owns the server that transmitted the email (which is typically
the
: culprit's ISP's computer unless the asshole is running his own mail
server).
: The IP Block returns information about who owns the range of IP addresses
: into which our spammer falls. This is crucial for making contact upstream
of
: the sender. Finally, the Traceroute provides a transcript of machines
that
: lie between SamSpade.org and the target IP address.
: Let's see what comes up from
the queries.
|

