- ... Unix2.1
- By
Unix, the author means all the Unix derivatives (Linux, Solaris, BSD)
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
POSIX2.2
- POSIX is a operating system interface standard. Most
unix-like systems aim for POSIX compliance.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... building3.1
- Actually, make
could be used to automate almost any task. However, it's used almost
exclusively for program construction.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... makefile3.2
- Any
text after a # character is considered a comment and is ignored by Make
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... points5.1
- Extensive use of the GOTO
statement, found in many languages, is largely considered poor
programming practice. GOTO makes it extremely difficult to
reason about the execution order and correctness of code.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... segfaults5.2
- A segmentation violation is an error
in which a program tried to access memory that has not been
allocated to it
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... code6.1
- Donald Knuth asserts, ``In
non-I/O-bound programs, less than four per cent of a program
generally accounts for more than half of its running time.''
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... numbers8.1
- The
reader will quickly see that
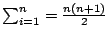 , which can be
calculated using only an integer addition, and integer mulitply, and a bitshift.
This is a good example of how a little thought about the problem usually provides
more benefit than clever programming techniques.
, which can be
calculated using only an integer addition, and integer mulitply, and a bitshift.
This is a good example of how a little thought about the problem usually provides
more benefit than clever programming techniques.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... threads8.2
- Threads can be thought of as a lightweight
process. They incur less operating system overhead and scheduling penalities than
an process. A process may have many threads of control, determined
by the operating system and/or system administrator
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... worker8.3
- The
author suggests setting DEFAULT(NONE) so that variables are not
automatically scoped private or shared.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
path8.4
- The absolute path is the fully qualified name of the
file. For example /usr/bin/ls rather than just ls or
bin/ls.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... network8.5
- Performance
tip: if reading or writing temporary files during a calculation,
don't use filesystem that is mounted over the network. use a local
disk
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... hosts8.6
- Either DNS names or
IP addresses
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... IEEEA.1
- Institute of Electrical and Electronics Engineers
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... UnixA.2
- Mac
OSX includes the OpenSSH client ``ssh''
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... cryptographyA.3
- Public key cryptography allows the
encoding key to be revealed without weakening or compromising the
security of the encoded message. OpenSSH uses the RSA system
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... passwordA.4
- However, most OpenSSH
servers are configured to fall back to regular password
authentication if other authentication methods fail.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... integerA.5
- UID 0 is reserved for the
system administrator and super-user, root
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...bashA.6
- Bash is the Borne Again SHell which is developed
as part of the GNU project. Most Unix machines have a version of
Bash available, even if it's not the default shell.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... programA.7
- In the simplest model this means interpreting the contents of the file as
instructions, but a complete treatment of program loading is beyond
the scope of this document.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... contentsA.8
- The names of the files in
the directory, not the contents of the files themselves.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- .....)A.9
- These are
special directories. . always points to the directory that
it's in, and .. always points to the current directories
parent directory.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
timesA.10
- Under certain circumstances, programs close the
standard file handles or replace them other files
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... ScreenA.11
- C-a C-d
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... functionsA.12
- Users can control where man
searchs for manuals with the MANPATH environment variable.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
variableA.13
- See A.3.3
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.